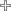Course Outcomes: After learning the course the students should be able to:
|
Course Code |
Course Outcomes |
|
ECPL215.1 |
Discuss cryptography and network security concepts and applications. |
|
ECPL215.2 |
Identify security attacks and services. |
|
ECPL215.3 |
Use symmetric and asymmetric key algorithms for cryptography. |
|
ECPL215.4 |
Examine the issues and structure of Authentication Service and Electronic Mail Security. |
|
ECPL215.5 |
Apply security principles to System design |
Mapping of COs with POs-PSOs:
|
Course Code |
PO1 |
PO2 |
PO3 |
PSO1 |
PSO2 |
|
ECPL215.1 |
2 |
- |
3 |
1 |
1 |
|
ECPL215.2 |
2 |
- |
3 |
1 |
2 |
|
ECPL215.3 |
3 |
- |
3 |
2 |
2 |
|
ECPL215.4 |
3 |
- |
3 |
2 |
2 |
|
ECPL215.5 |
3 |
- |
3 |
2 |
2 |
|
ECPL215 |
3 |
- |
3 |
2 |
2 |